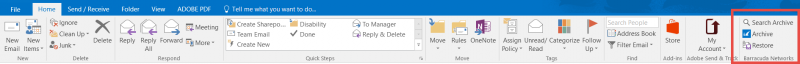
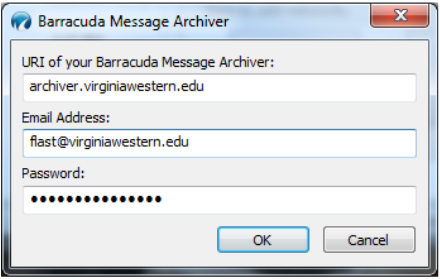
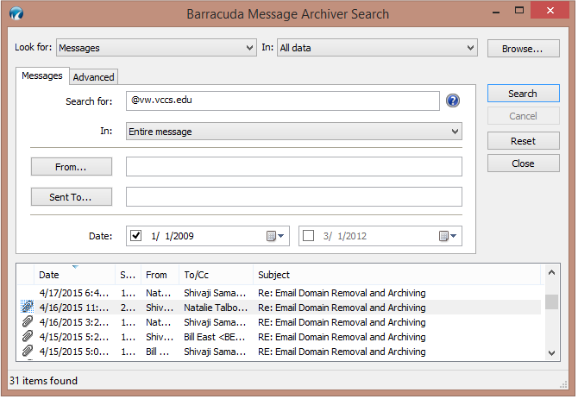
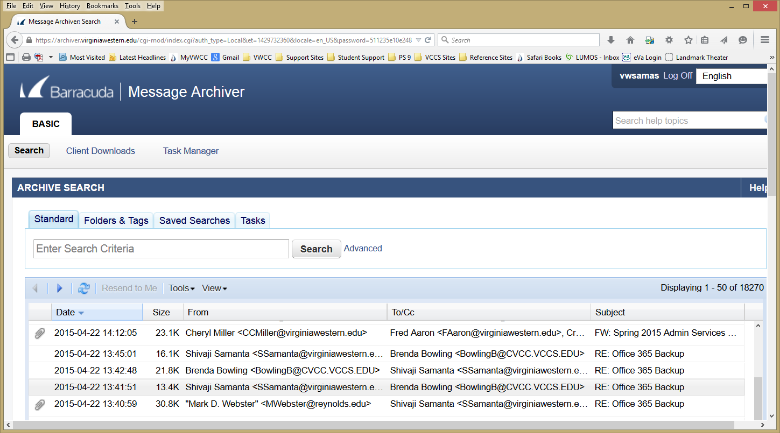
This guide is to be used by supervisors to set up a new employee with network access.
Does the new employee’s office have a computer and phone?
If Yes: If the room already has a computer and phone then you should complete a SARF (see below) so that access setup can begin.
If No: If there is not a computer and phone in the office, you should still complete a SARF (see below) but after completion you also need to contact the Help Desk and request a ticket be opened for a computer and phone install. Please inform the Help Desk that you have completed a SARF.
What is a SARF and how do I complete it?
The SARF is the college’s Security Access Request Form. This form is used to request computer and phone access for employees. For more information about the SARF, please refer to Security Access Request Form (SARF).
How do I know when my new employee’s access has been set up?
A “Welcome Email” will be sent to the employee’s VWCC email account along with a copy to the supervisor. As the supervisor, you should provide the employee with a copy of the email to assist in accessing their new accounts.
What is the K: drive and how does my employee get access?
The K: drive is a network drive that is available when using academic computers located in labs and classrooms. It allows both students and instructors to see the files without having access to edit them.
In order to access the K: drive, a user must log in to their administrative account. Contact the Help Desk if a folder needs to be created.
Is there any training for new employees?
Online New Employee Information Technology Orientation
IET has an online orientation available for new employees. The orientation can be accessed here. Please let the Help Desk know when orientation has been completed.
Security Awareness Training
As part of the Commonwealth of Virginia information security standards, employees are required to complete Security Awareness Training within 30 days of receiving their welcome email. Additional information can be found on our Security Awareness Training page.
How does my employee get access to a Virtual Desktop?
All faculty and staff have access to a virtual desktop. Using a virtual desktop allows access to VWCC cloud services such as mapped drives, printer access and VWConnect from anywhere. A virtual desktop can be accessed via a variety of end users devices, such as a thin client computer, desktop computer, iPad, iPhone, or other mobile devices. All VWCC owned computers have the hosted desktop VMWare View Client installed on them. For more information, refer to our Virtual Desktop page.